MMD-0012-2013 - ARP Spoofing Malware Infection Project Disclosure
29 Dec 2013 One more 2014 New Year Malware Awareness Message from MalwareMustDie:Self spreading malware project to infect other nodes using ARP spoofing based scanner was spotted back in several month, our intelligence reported and we keep on monitoring its progress ever since, and the moronz involved just has been released in the cyber criminal's forum. The malware works practically by controlling the usage of ARP broadcast to be as stealth (not noisy) as possible to spoof the ARP packets and grabbing nodes information for determine the target for the infection. The method is simple, yet worked (as per quick tested).
Currently the code was "secured in to our hand" and of course we informed several industry and trusted researchers for this new threat, but after compiling and test AV scanning found the detection ration is still very low, wondering why..
Assuming the threat is NOT handled as "priority" by industry's side we think is better to raise awareness of this threat's existence is needed, that's why we disclose the codes in here, to aim overall malware researcher community's attention.
We also think is important to eliminate the threat from their ground zero when they're first spotted, not necessarily wait until becoming popular or epidemic., so if there is a clear shot to be taken, hammering any effort in improvement of any form malicious method is the only MMD main mission from beginning. Explaining the additional reason of this disclosure.
For the authenticity of the above statement, below is the message snagged from a known moronz forum, about this evil-product's release post, you go figure which forum it is. To be frank, if you are a security industry entity and you are not noticing this, is time to for you to put more effort budget on intelligence work instead:
This moronz is actually releasing the product and seek for buyers (promotion). The package we snagged is a full code of project of this malware,and currently the commercial version was spotted too including the pcap installer inside.
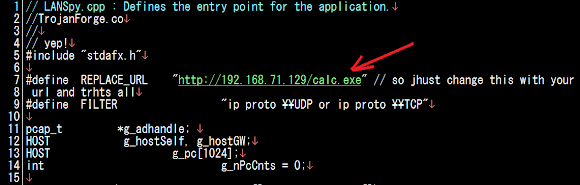
And this is the text of the malware release notes, you'll see here how the project was built:
The payload of the threat is infection of ANY executable file (not specifically a PE file, noted this well) in windows platform. As per seen in the below source code snips taken from the project's code:
//xxxxxxx
========================================================================
WIN32 APPLICATION : LANSpy Project Overview
========================================================================
AppWizard has created this LANSpy application for you.
This file contains a summary of what you will find in each of the files that
make up your LANSpy application.
LANSpy.vcxproj
This is the main project file for VC++ projects generated using an Application Wizard.
It contains information about the version of Visual C++ that generated the file, and
information about the platforms, configurations, and project features selected with the
Application Wizard.
LANSpy.vcxproj.filters
This is the filters file for VC++ projects generated using an Application Wizard.
It contains information about the association between the files in your project
and the filters. This association is used in the IDE to show grouping of files with
similar extensions under a specific node (for e.g. ".cpp" files are associated with the
"Source Files" filter).
LANSpy.cpp
This is the main application source file.
/////////////////////////////////////////////////////////////////////////////
AppWizard has created the following resources:
LANSpy.rc
This is a listing of all of the Microsoft Windows resources that the
program uses. It includes the icons, bitmaps, and cursors that are stored
in the RES subdirectory. This file can be directly edited in Microsoft
Visual C++.
Resource.h
This is the standard header file, which defines new resource IDs.
Microsoft Visual C++ reads and updates this file.
LANSpy.ico
This is an icon file, which is used as the application's icon (32x32).
This icon is included by the main resource file LANSpy.rc.
small.ico
This is an icon file, which contains a smaller version (16x16)
of the application's icon. This icon is included by the main resource
file LANSpy.rc.
/////////////////////////////////////////////////////////////////////////////
Other standard files:
StdAfx.h, StdAfx.cpp
These files are used to build a precompiled header (PCH) file
named LANSpy.pch and a precompiled types file named StdAfx.obj.
/////////////////////////////////////////////////////////////////////////////
Other notes:
AppWizard uses "TODO:" comments to indicate parts of the source code you
should add to or customize.
/////////////////////////////////////////////////////////////////////////////
Below is the video of this disclosure, the video contains code snapshots, libraries & overall files, archive names + hash, and how to contact us for getting the source. See this video well before you requesting anything to us, the video was made by our team, contains enough information to satisfy your curiosity to confirm about the maliciousness of the software. But I do not include any compilation, any build process related to this source, we don't compile and avoid any effort in production of these except for detection rates testing purpose one time, we deleted the materials. Now we leave it for you to analyze, test and research. Moreover, this is the evidence of the cyber crime, so we don't feel to share this to everyone. By seeing the code, one is expected to learn the concept that is being used to code ARP spoofing malware infection. And researching the best way/method in mitigating the threat if the infection starts. For real, it will be a hard effort to stop it instantly once a security perimeter is breached by this malware installation, and any computer device just don't block ARP broadcast by default. So we urge to you to test it and see how it works too, not only taking sigs and leave it as per it is. I expect seeing report on fellow researcher's blog about the report of this mess. Our team is making a very hard effort for informing this, do not mock this disclosure but take it positively, and take a look at the materials, and it is time to read the codes.
Let us warn you again: this is NOT malware sample but a malware SOURCE CODE, not a stuff that can be openly shared, we share to law enforcement, AV industry & security scanner products & vetted trusted researchers as the first priority, for sharing purpose. So if you related to those entities, prepare FTP account for us to PUSH the data into yours, and we're sorry that we need a legit emails/comm for this, it is not dealing with individuals but with your entities, please do not hesitate to contact.
For the malware moronz, if you think we don't watch you closely THINK AGAIN! Stop your evil coding practice before is too late, if beloved God blessed your stupid head to make code and please use your skill to code good system or application to make an honest living instead. Even if life is unfair to you that's NEVER be a tolerable excuse to keep on making new shits.
So you are warned, payday will come soon, we're assuring you we're different to any form that ever deals with you, we're straight coming to you.
This post is dedicated to MMD Georgia, a country of crusaders.
#MalwareMustDie!