MMD-0032-2015 - The ELF ChinaZ "reloaded"
20 Jun 2015The background and recent info of ELF ChinaZ
The report and analysis of a new variant of Linux/ChinaZ ELF malware spotted in the wild
This post is written in a relax time, so please enjoy reading it in your weekend.
MalwareMustDie (MMD) group found new ELF malware called ChinaZ reported in the previous post in→January 2015 while it was riding the Shellshock for infecting Linux boxes in the internet. And the new version of ChinaZ was accidentally spotted while our team was gathered to scan internet for more ELF bad stuff, and we were all in sleepy mode after our day work in weekend...picture↓ :) 
As also described in the previous post,ChinaZ is a new type of its kind that raises from the mainland China DDoSer land. Adapting some of techniques & codes used by previous China ELF malware, and coded with the C (without plusplus) using an "original" interaction method to linux system during its infection, is showing the coder knows Linux very well and he has potential to make better stealth ELF malware with his knowledge. Needless to say MMD is in the kind of "CTF mode" of cracking what he built every time he released new version.. we hope for authority to catch this man as soon as possible.
As a new malware, the ChinaZ malware is rapidly coded into some variants and the popularity is aggressively raising fast, it is adjusted to some vulnerability trend to support its infection efforts to linux boxes. It urged also an open development of its code too, a suspected related development branch of ChinaZ development source code even spotted in the GitHub and it looks actively coded until mid of March 2015, as per shown in the below link/picture. Yes, we have some samples that are perfectly matched to the codes released in this Github, and yes, this matter also has been reported to the law enforcement accordingly to be escalated to the PRC (read: people republic of China).
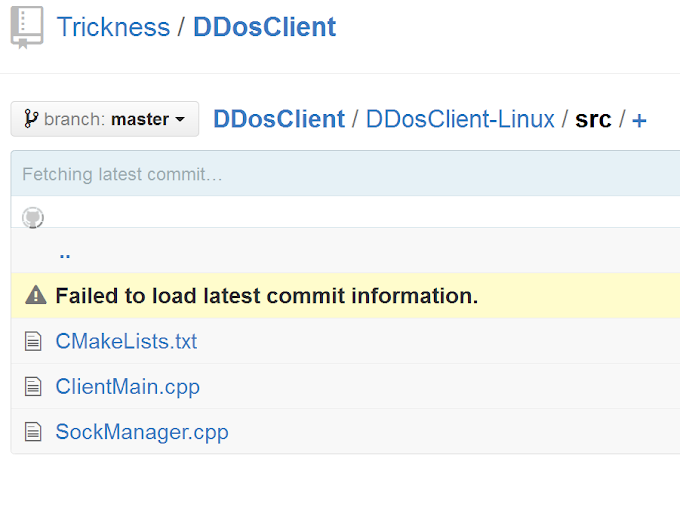
DISCLOSURE of #ChinaZ #ELF #malware coder (pic)
Reported this to LEA now
by #MalwareMustDie! to @FBI @INTERPOL_Cyber pic.twitter.com/iLLlzT3A9X
— ☩MalwareMustDie (@MalwareMustDie) July 26, 2015PoC: DDoSClient = ChinaZ
ChinaZ builder: https://t.co/Wq6i7Z8SIi
Matched code (pic) http://t.co/QObfCqZXBz
@biergaizi pic.twitter.com/P7XoWbrizU
— ☩MalwareMustDie (@MalwareMustDie) July 26, 2015These symbols are original vars, is ALL OVER the codes. NO , DON'T tell us this is NOT for DDOS! CheckMate @biergaizi pic.twitter.com/MEfbywF7XQ
— ☩MalwareMustDie (@MalwareMustDie) July 26, 2015I was asked to PoC recent of #ChinaZ #malware = coded by Trickness(coder). Here's MATCHED to today's #ELF x64 sample! pic.twitter.com/nelGOVH0ot
— ☩MalwareMustDie (@MalwareMustDie) July 29, 2015The "ChinaZ As Service" for DDoS'ing some targeted sites in the internet is also spotted in the wild, which is currently up and alive too. Below is the screenshot of its nice web UI used... This matter is in the investigation of the authority so.. sorry, we can not reveal more information than this, but please be aware of this information too:
Considering of the seriousness of the coder and his efforts to push the threat and its campaign further into the market, MalwareMustDie(MMD) the ELF team folks are studying and following the threat well by reversing the every samples spotted online.
How do we know this spotted one a ChinaZ?
Deep in the Hangzhou city in region Zhejiang in China mainland six hours++ ago, 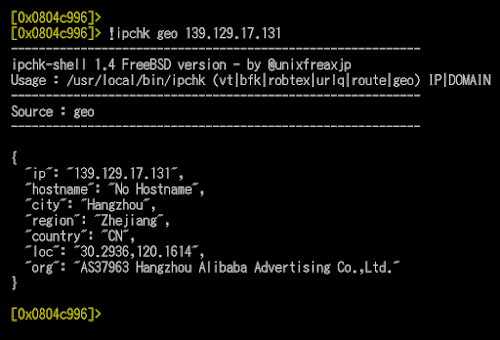
..there is a malware bad actor who has a dream to conquer the world by spreading a new variant of ELF malware on an infecting HFS web panel:
So his plan is to infect as many linux boxes that he can compromise, by fetching this ChinaZ binary at its panel via wget or fetch or similar methods/commands.Yes, this is the "comeback" of the previous crook with the same dream by using shellshock to infect 0.0.0.0, but it looks like he went to the classic ELF infection way now, drive-by download.
Too bad his dream was ruined now...
Knowing the series of this malware very well, I just spotted the right function to ID it:
The headers look usual too, a static and stripped ELF: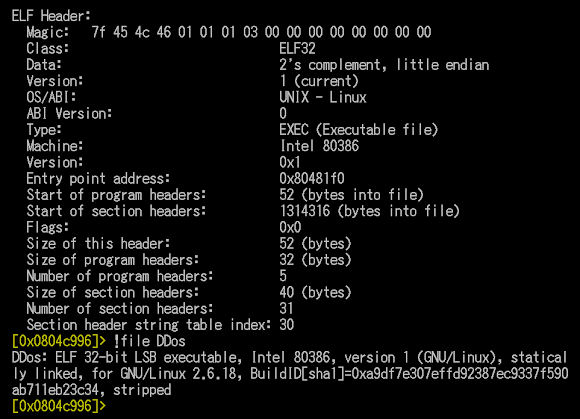
The author is trying hard to strip every strings related of ChinaZ that we posted in previous posts ("s" is for assuming that he reads also the kernelmode reports we posted too), but he forgot the fact that we are good reversers and reversed so many samples of previous ChinaZ already, so the basic characteristic of the code used are known very well..i.e.: symbols and functions in .cc malware source code files used to built ChinaZ are still "seen" here and there too (some hint: codecvt_members.cc , collate_members.cc , ctype_configure_char.cc , messages_members.cc , monetary_members.cc , numeric_members.cc . time_members.cc and so on..), and yet he is making the work easier too by still being possessed to use the same ridiculous botnet commands like:
..and the classic reason is...the coder just can not get rid of his fanatic brand of "chinaz" itself :-)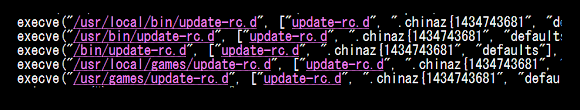
(later on, during the execution that name is used too in ↑dropped file).
How does it work?
The way this variant works is simple, let me try to explain it in one paragraph:
It is self-copied to the /tmp directory and that dropped one is being executed by the sample (which will be self-deleted afterward), and running installation scripts for (1)service registration, (2)file installation to other dirs, and (3)cron schedule setup, to then trying to connect to the remote host after flushing and modifying your iptables. It deletes your /etc/resolv.conf and save some initial setup and downloading configuration data (Config.ini), but not installing any rootkits. Connection to the CNC is by sending your uname info, and of course the IP address. To then communicate as bot under CNC connection established. The command sent from CNC are mainly designed for DDoS commands with parameter of a target IP address.
To be more details, the execution command list can be seen in here-->[LINK]<--along with its networking process including the CNC calls for domain, IP and ports. After these installation steps executed the infected host will be rebooted, and ready for action as a remotely controlled DDoS bot.
Below are screenshots on how it works as proof:
The ChinaZ daemon script, to be copied in the /etc/init.d/%s/ and /etc/rc%d.d/S90%s, in our case the $s value is a fake process/binary called "ConfigDatecz": 
The autostart by injecting a one-liner startup command to the crontab (scheduler) to execute ChinaZ startup script on hourly schedule: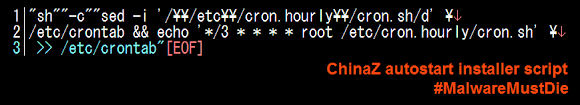
The malware's script to control the network interface, by utilizing ifconfig and the usage of udev self explanatory: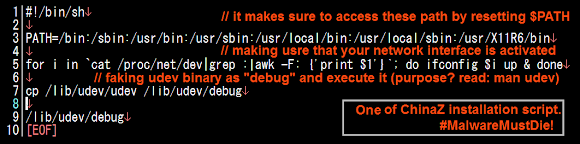
The reboot command after all malware setting has done, is like this sequence:
Yes, by the way he starts to curse a lot now.. I bet he is under a lot of stress recently... :)
Below is one of typical command of ChinaZ malware does, so this another proof that it is not Linux/Elknot, not Linux/XorDDoS but Linux/ChinaZ, a known one:
The self-copied file naming proof: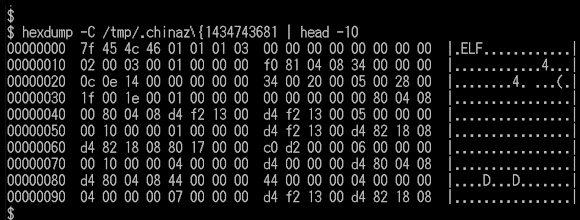
The DDoS sent via HTTP's GET command (template) to be sent to the target, noted that QQ (China version of ICQ) account details, is a suspected this malware coder's signature: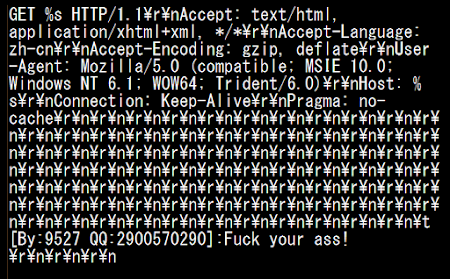
The hard evidence of DNS request for the CNC domain of www.vttx.cn can be seen in here, if you in doubt with the syscall codes in the paste:
..showing the CNC IP address 121.42.159.37:
The GeoIP of CNC is in here, well it says "Hangzhou" the same area where the HFS payload is:
"ip": "121.42.159.37",
"hostname": "No Hostname",
"city": "Hangzhou",
"region": "Zhejiang",
"country": "CN",
"loc": "30.2936,120.1614",
"org": "AS37963 Hangzhou Alibaba Advertising Co.,Ltd."
Any ID of the actor?
Domain registration shows the registrant (maybe fake) name and email address, this domain was just registered this month:
Domain Name: "avttx.cn"
ROID: 20150606s10001s76116835-cn
Domain Status: ok
Registrant ID: hc-199918169-cn
Registrant: "时红林 (Shi Hong Lin)"
Registrant Contact Email: "[email protected]"
Sponsoring Registrar: 阿里巴巴通信技术(北京)有限公司(原万网)
Name Server: dns9.hichina.com
Name Server: dns10.hichina.com
Registration Time: 2015-06-06 18:54:24
Expiration Time: 2016-06-06 18:54:24
DNSSEC: unsigned
Virus Detection Ratio, Samples and Indicators
The detection ratio is not so bad, During the first initial check in VIrusTotal, 4(four) major antivirus products can detect this new variant by their signature already. Good work!! :-) 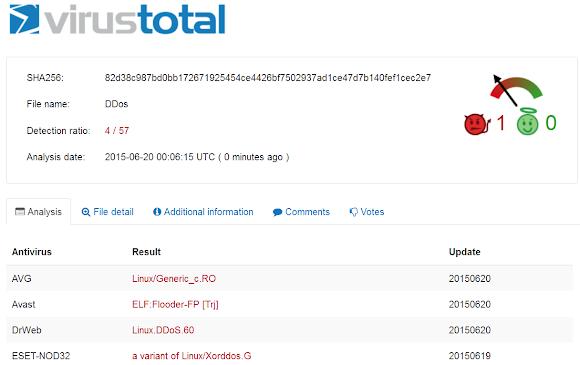
Sample is shared for researchers via kernelmode-->[LINK]
Indicator for detecting this malware can be defined well in non-Linux platform too, and Mr.Marc Ochsenmeier, our friend and author of PeStudio was demonstrating how the blacklisting of strings used in this ELF can be used to detect this ELF in Windows OS too, prior its checking to anti malware detection utility. Below is the tweet & pic (noted, it is a demonstration only, the strings blacklisted are samples):
@Cyb3rOps The ELF ChinaZ #malware offending indicators #pestudio @MalwareMustDie pic.twitter.com/W9jqYeUZyg
— Marc Ochsenmeier (@ochsenmeier) June 20, 2015Prologue and additional section
In the end, please care of your NIX box's security, make sure you secure it up properly and know exactly what is running inside. Make backup regularly on the binaries and data too & stay safe!
Due to the rapid abusive activity coming from PRC (people rep of China), and if your infrastructure is not related to and you don't have any business to conduct with them, it would be one of some options to secure your network perimeter by blocking ssh access coming from China and Hongkong networks. Due to the minimum resource for the mentioned list, we made and currently maintain PRC and HK network block data for the purpose, together on the example on how to use them in: hosts.allow (TCP deny rules for multi platform), iptables (drop rules), ipfw (xBSD) and htaccess. So if you are interested please feel free to use them as per it is as per announced in the below tweet, if any additional or correction for the list please ping me here at the blog comment or in the twitter.
I maintain China/HK IP blocklist: https://t.co/ErE2Wozj6q
added: 101.227.0.0/16 182.96.0.0/12 43.229.52.0/24 43.255.188.0/24
#MalwareMustDie
— MalwareMustDie, NPO (@MalwareMustDie) June 21, 2015Some work appreciation from China crooks:
This kind of "I love you" attack always come right after #MalwareMustDie exposing "bad stuff" from PRC/#China :) pic.twitter.com/Ux5xEHVk43
— MalwareMustDie, NPO (@MalwareMustDie) June 22, 2015#MalwareMustDie!